This guide explains the basics of the strategy phase in HEATED, from the game’s goals, mining currency, using the terminal, and hacking your opponent.
Currencies and Miners
In the strategy phase, you are given two crypto miners to mine two different types of currency, Hierro (ITC) y oro (GTC).
Iron is used to purchase items from the Shop, including more miners, generadores, and software. Feel free to spend as much of this as needed, as Iron is useless outside of the strategy phase. para empezar, you are given a few Iron miners to start depending on the largest teams size. (If the largest team in the game consists of three players, each team is given three iron miners to start.)
Oro isn’t as useful in the strategy phase, however is vital to win the phase. Gold is used to purchase weapons, munición, armadura, and other gear that will be used in the proceeding action phase, so gather as much as you can. Además, the team with the most gold at the end of the strategy phase scores a point, so keep an eye on your opponent and make sure you’re doing everything possible to get more gold than them.

Additional miners can be purchased via the shop. Keep in mind that each miner requires three modules of energy in order to properly function, so it’s highly recommended you purchase a generator in addition to a miner. (Generators will automatically allocate to an un-allocated miner and vice versa). If you run out of spots for generators, energy can be split among them, or energy can be unallocated from another miner.
Generators and Energy
Generators are used to provide power to crypto miners. They are purchased from the shop and spawn in the room opposite the mining room. Each generator has three energy slots that it can provide, which can be split among different miners.
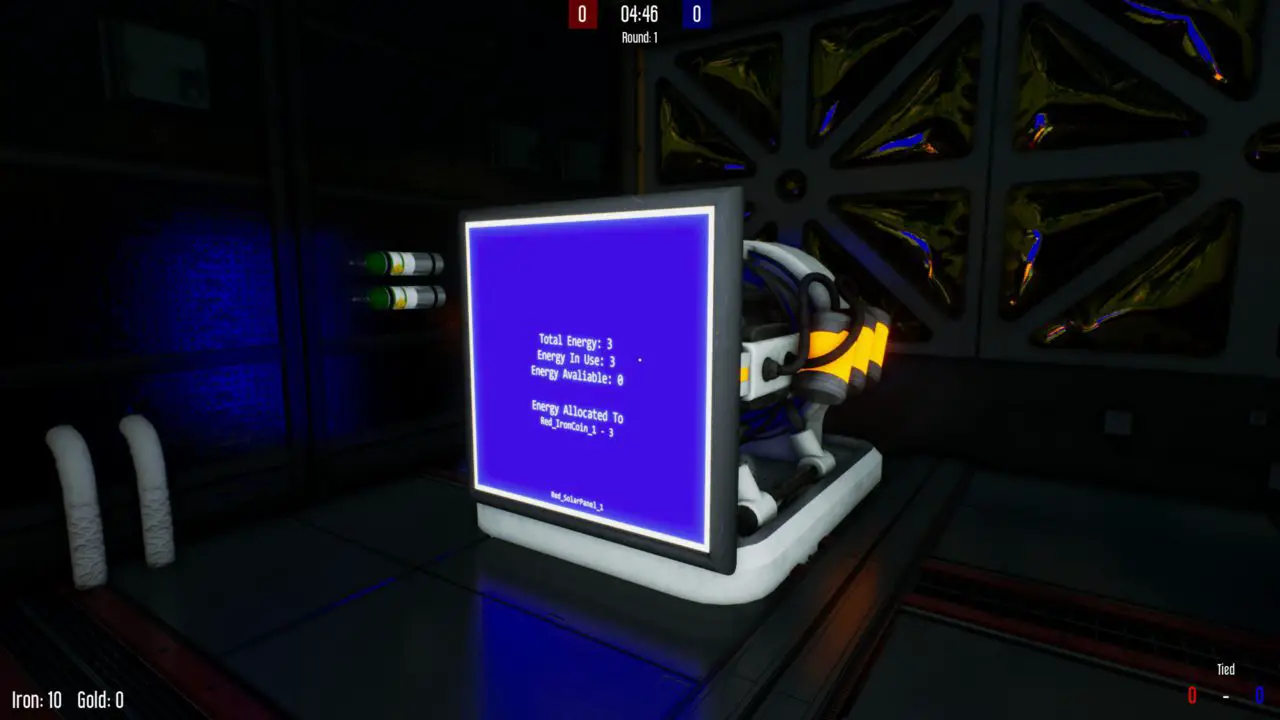
To control generators, you must use the terminal. There are two commands that you can use. Estos son, allocate and unallocated.
Allocate gives miners a set amount of energy that is used to increase mining speeds. Each miner can have a maximum of three energy slots allocated to it. Primero, find the name of the generator you want to allocate energy from, and make sure it has enough energy available. Look at its screen and you’ll find the name of the generator at the bottom. Entonces, find a miner to allocate that energy to, again looking for the name at the bottom of the monitor. Entonces, specify the number of slots to grant it, que van desde 0-3. (en la mayoría de los casos, you’ll be using three.) Entonces, run to the terminal, and type the command shown below:
Asignar <Generator_Name> <Miner_Name> <Number of Energy Slots>
Por ejemplo, if you are allocating three energy slots from Red_Generator_0 to Red_GoldCoin_3, the command would be: allocate Red_Generator_0 Red_GoldCoin_3 3.
Unallocated simply removes all energy allocations the generator has. This can be used to provide more energy to other miners, or when hacking. The command is simple.
unallocate <Generator_Name>
Por ejemplo, if you are unallocating all energy from Red_SolarPanel_2, the command would be: unallocate Red_SolarPanel_2
The Terminal
Terminals control all the technology in your base and can be used/hacked to provide access to your opponent’s infrastructure. This is located between the generator and the mining room.
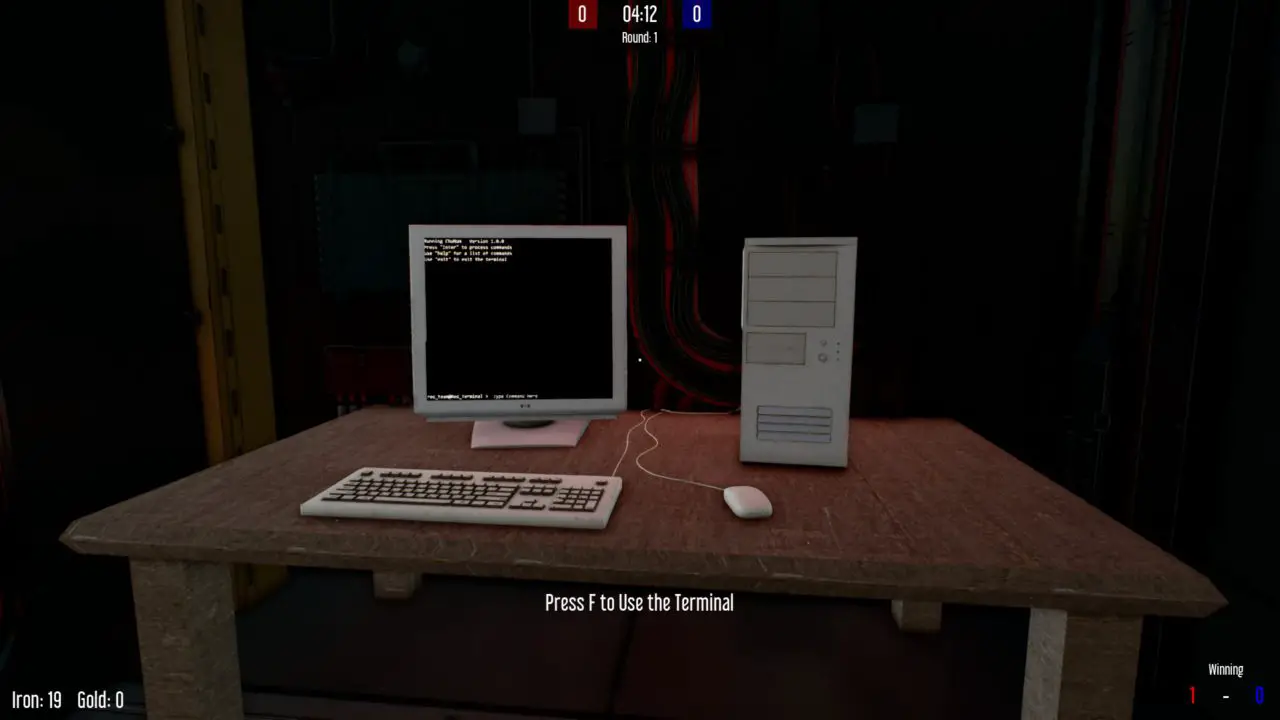
The terminal provides an autofill menu if you are using a controller or you don’t know the commands, sin embargo, you may type it yourself if you wish. Upon interacting with the terminal, you are able to begin typing commands.
These are the basic commands:
- Ayuda – Displays the help text. This gives you a rundown of every command.
- Salida – Exits the terminal
- Lista – Lists all the technology of a certain category. Tipo «lista» and hit enter to see what you may search for, then input it into the command following this syntax: lista <artículo>. You may also use list all to show every item available.
- Allocate/Unallocate – Described above
- Eco – Displays text on the terminal. Follow it up with a string (Ejemplo: echo hello world prints Hello World.) This can be used to taunt hacked opponents.
- Conectar – Connects to another terminal. This will then allow you to run commands on the other team’s infrastructure. (This is described more in-depth in the hacking section.)
- Desconectar – Disconnects you from a different terminal.
- Claro – Clears the screen
- Ejecutar – Executes malware. You cannot run this on yourself and must be connected to another terminal.
Seco
Ofensa
To hack, you need software. All software can be purchased from the shop in the Software tab, followed by checking the various tabs to help you navigate programs for offense, defensa, malware, o «essentials.»
A quick note on software: All software is purchased from the shop, and comes in three levels. Each level allows the program to run quicker, (or in some cases, grant you some extra time). A description of what the program does at higher levels will be provided.

Hacking is performed in three steps:
- Fetch the opponents key
- Decrypt the key
- Connect to them and start hacking
Fetch the key
- To fetch the key, you need to purchase the software KeyFetch from the shop in the «Ofensa» pestaña, which will cost you about 15 hierro (multiplied by the level you are purchasing). After anyone on your team purchases KeyFetch, run it at the terminal by typing «keyfetch <Terminal Name>»
Decrypt the key
- Después de algún tiempo, you’ll receive a message on your terminal stating that the encrypted key has been captured. To decrypt the key, purchase the KeyCrypt program from the shop in the «Ofensa» pestaña. After purchasing it, run it at the terminal by typing «keycrypt <Terminal Name>»
Conectar
- You’ll receive a notification again once the key is decrypted. (No te preocupes, you don’t need to remember the password that is displayed.) En este punto, your opponent’s terminal is cracked open and ready for you to run commands on their infrastructure. To connect, Simplemente escriba «connect <Terminal Name>»
After you are connected to your opponent, you’ll notice the name in the bottom left changes. Desde aquí, any command you enter will run on your opponent’s infrastructure. Now is a great time to begin executing malware, un-allocating their generators, or even allocating their generators to your own miners. Disconnect at any time by typing «desconectar»
Malware is a great way to lock up your opponent and set them back. Malware can be purchased from the shop and can only be used once. Malware, like all software, has levels that make it difficult for the anti-virus to detect and eliminate the virus, sin embargo, each level comes at an extra cost. To use malware, connect to your opponent’s machine then type «execute <malware name>»
If you don’t have malware, or you want to further complicate your opponent’s plans, I recommend un-allocating all their generators. You can do this using the «unallocate» command from before. A great attack method is to execute URMINENOW, then un-allocate everything. This locks up your opponents from re-allocating their generators and keeps them stuck with 0 energy until their anti-virus removes the virus.
Malware: URMINENOW – Locks up your opponents terminal, preventing them from entering commands
Defending Against Hacks
Defense is done passively using the software. All software is passive and does not require any user interaction to work after you purchase the program.
To defend against your opponents accessing your terminal in the first place, purchase the Encryptor program. That encrypts your key making it harder for KeyCrypt to decrypt it, and buying you some time. (NOTA: After your opponents fetch your key with KeyFetch, this will have no effect. If you received a warning that your opponents captured your key, don’t buy this.) You can also purchase «KeyLock,» which makes it harder for your opponent to access your key with KeyFetch.
If your key has already been compromised, purchase anti-virus and a firewall.
The anti-virus will remove malware after it is executed by your opponent. This will take time, which can be reduced by buying higher versions. This program is passive, and no user interaction is required to remove the malware. A message will appear on the terminal if it detects and is removing malware.
The firewall will disconnect your opponent after a certain amount of time. Depending on your firewall’s level and your opponent’s IP Bouncer level, it will automatically detect, and disconnect foreign connections.
Eso es todo lo que estamos compartiendo hoy para este HEATED guía. Esta guía fue originalmente creada y escrita por Marinara Sauce. En caso de que no actualicemos esta guía, puede encontrar la última actualización siguiendo este enlace.
